We’ve been focused on the wrong spies. When 11 Russian sleeper agents were discovered living in the United States—and then sent home in exchange for their counterparts—it was hard to resist the sexy espionage tale with echoes of the Cold War. But while we’ve fixated on Anna Chapman and her cohorts, top diplomats were working on a wonkier but more important advance in spycraft. This month, experts from 15 countries agreed to begin serious negotiations on establishing international norms on cybersecurity. This story is far more significant in the long run because, without basic agreements about cyberspace, cyberattacks, and even cyberwars could become a daily danger.
Tuesday, February 8, 2011
Spyware in the office
What's far more likely is that corporate laptops and desktops include outdated, misconfigured and even unapproved applications. Users might download free games, utilities and media players on their corporate laptops or desktops or install peer-to-peer file-sharing programs.
In many cases, use of such utilities and programs is against corporate policy and a security risk to the organization. Why? Because many of these popular programs include spyware.
Threat or nuisance?
Spyware, sometimes called adware, snoopware or sneakware, is software that secretly gathers information about a user and relays that information to another party over the Internet. In many cases, users unknowingly install spyware when they download freeware or shareware, even though references -- often obscure -- to spyware might be included in the program's end-user agreement. In other instances, spyware programs are automatically installed when a user simply views an HTML e-mail or visits a certain Web page.
At its mildest, spyware is a simple tool used by advertisers to track users' Web-surfing preferences.
At its worst, spyware is used to monitor keystrokes, scan files, install additional spyware, reconfigure Web browsers, snoop e-mail and other applications, and more. Some of today's spyware can even capture screenshots or turn on webcams.
In a corporate environment, these capabilities pose a major threat to corporate security, especially since much of this activity goes on without anyone's knowledge.
Even in computing environments that encrypt data, spyware remains a threat to the security of corporate data because its keystroke-logging components capture input before it's encrypted.
An aid to spam
But that's not all. Spyware also leads to spam and vice versa. When spyware finds e-mail addresses, it sends them back out over the Internet to be traded, shared or sold to spammers. When unsolicited commercial e-mail finds a user who clicks to see an advertised product, spyware secretly downloads as the advertisement unfolds. This creates an administrative nightmare for corporate IT professionals, not to mention the legal implications it introduces as inappropriate content floods in-boxes.
Spyware also consumes memory and system resources. Because it constantly phones home to deliver user information and then sends back more pop-ups, banner ads
Three steps for defending against internal threats
For years, computer security experts and analysts have been talking about internal threats to enterprise information, yet no elegant solutions have presented themselves. Risks from internal threats are the most difficult to defend against and are generally more damaging than better-known external threats.
Companies today face a delicate balance between empowering employees and protecting corporate resources. Today's firewalls go well beyond traditional packet-header inspection; instead they examine packet contents and reassemble traffic to investigate the data in its intended formats. This progress comes as shifts in the market have reduced costs. It's time to rethink internal enterprise security options.
First let's look at some of these key threats -- worms and internal hackers.
Disruptive worms
Worms such as Mydoom and Sobig are among the latest internal threats. A worm will typically be launched externally, but once inside a network, the IT administrator and staff must stop the worm and minimize the internal damage from the infestation. Blended threats are extremely disruptive, consuming corporate and IT resources to stop their effects and repair damaged systems. Each new worm is more complicated and destructive than the last.
Internal hackers
Once a hacker has access to a network, his work is generally three quarters complete. An internal hacker might be a strong technical resource within an organization. With a keycard to enter the building, the hacker might have all the authorizations needed within a typical enterprise to access just about any information needed. This employee level of access is the main reason internal threats are so detrimental. Further, the introduction of wireless technology into the workplace and the general acceptance of telecommuting have all but made physical security obsolete.
Technology advances, markets shift
Advanced threats combined with market and technology shifts are encouraging businesses of all sizes to deploy enhanced internal threat protection. Meanwhile, the cost of security technology has dropped considerably over the past few years as technologies like firewalls and VPNs have become commodities. As these traditional technologies mature, efforts are made to extend the life of existing security and networking equipment as with complementary departmental gateway antivirus devices.
Below are three simple and relatively inexpensive steps your company can take to better defend against internal threats.
1. Deploy 'intrawalls' (firewalls between departments)
Firewalls are commonplace and
Top execs urged to zero in on security
Making the issue a top-level focus would alert more companies to the dangers and costs of viruses and computer break-ins, as well as improve overall national security, the group said.
Microsoft investigates 'download warning' flaw
On Monday, French Web site K-otik published exploit codes that could take advantage of the vulnerability. On Tuesday, a Microsoft representative said that the risk from the flaw is low because "significant user interaction and user interface steps have to occur before any malicious code can be executed."
However, the software giant did admit that it was possible to bypass the security warnings in IE--even when using Windows XP with Service Pack 2.
"Microsoft is investigating this method of bypassing the Internet Explorer download warning and will take appropriate action to cover this scenario in order for customers to be properly advised that executables downloaded from the Internet can be malicious in nature," the representative said.
The representative acknowledged that if the file were saved in the start-up folder, it would automatically run the next time the user restarted his computer.
"The user must go to the folder containing that executable and choose to run it, or log off and log back onto the computer if the attacker attempted to save the malicious executable into the user?s Windows start-up folder," the representative said.
However, the representative said the problem was not a security vulnerability but actually a clever use of social engineering.
"It is important to note that this is not the exploitation of a security vulnerability, but an attempt by an attacker to use social engineering to convince a user to save an executable file on the hard drive without first receiving the Internet Explorer download warning," the representative said.
Still, some security experts disagree with Microsoft on this point.
Sean Richmond, senior technology consultant at antivirus company Sophos Australia, agreed that the exploit would require some user interaction but said this was definitely bypassing a security feature in IE and SP2.
"This is certainly something that is bypassing some of the security features that are meant to be there. It is a way of bypassing the dialogs in IE. It will result in the (malicious) file being saved on the user's computer," said Richmond, who added that the matter would be worse if that file could be saved in a computer?s start-up folder.
Richard Starnes, an information security professional with around 20 years' experience in information security, incident response, computer crime investigation and cyberterrorism, said that legislation could be used to force Microsoft--and other software developers--to improve their code and take financial responsibility for their customers' losses.
"I wonder how solid Microsoft's coding would become if strategic governments around the world removed the liability shield that software manufactures now currently enjoy," Starnes said. "They would then have some real financial incentive to get it right the first time, instead of this Computer Science 101 coding they are continually churning out."
Starnes believes the quality of software development has fallen in the past two decades.
"Most commercial releases of software today wouldn't have made it out of beta 20 years ago," he added.
Super stealthy Internet messaging method revealed
A pair of Princeton University researchers presented a paper this week on a method for sending secret messages over existing public fiber-optic networks.
Princeton's Bernard Wu and Evgenii Narimanov made their presentation at the annual Optical Society of America meeting in Rochester, N.Y.
Their encryption technology is hardware-oriented and uses the properties of optical fiber to disguise a message. The technique involves sending a signal so faint that it is hard to detect or unscramble, because it is hidden by the natural optical noise of the network.
More specifically, the technique involves use of commercially available optical CDMA encoders that spread short, intense pulses of light carrying messages. The recipient decodes the message using information about how the message was spread out in the first place, plus compression gear.
Wu said in a statement that he does not believe anyone is using this method yet, because optical CDMA technology is still undergoing much research. He also said there could be a speed tradeoff for increased security.
The paper presented is called "Achieving Secure Stealth Transmission via a Public Fiber-Optical Network."
As with any supersecret network technology, the benefits to companies and government agencies would need to be weighed against the benefits criminals could gain from a way of sending undetectable messages.
Cyber-security new year resolutions for 2007
Consumers have been led to believe that hacker attacks and social engineering outbreaks will be on the increase over the holiday period, but the chances are that not many users have prepared a checklist to go through to make sure they're secure.
Security firm Perimeter eSecurity claims that users should take six key steps to ensure the maximum possible computer and network security as New Year's Eve approaches in an era rife with data theft, record levels of spam and increasingly innovative computer fraud.
"It doesn't take very long to enhance the security of a computer or its network," said Andrew Greenawalt, founder of Perimeter eSecurity.
"Whether you have a small business network or a vast business enterprise, these seven steps are imperatives to optimise your security as the New Year approaches."
Step One - Change every password you can find before New Year's Eve
Every online commerce site visited, every computer, and any other password-protected device or website will be security enhanced with this simple, time efficient move. Avoid easily discovered passwords such as names or numeric series, and resolve to change your passwords at least quarterly in 2007.
Step Two - Download patches and updates
Even the least expensive computer security programs offer downloadable updates or patches that can detect the latest viruses, close backdoors that hackers have discovered, or otherwise enhance network protection. Network owners with less thorough security programs should resolve to check and update patches on a monthly basis.
Step Three - Hire a hacker
Network owners should use the holiday lull to conduct a penetration test to identify weaknesses in network security. Instead of attacking databases and ne twork tools, these scans report back on specific vulnerabilities and recommend ways to solve the problems they identify.
Step Four - Conduct regular check-ups and keep your network safe by scheduling ongoing risk assessments
Automated monthly remote risk assessments can be conducted for less than the cost of a single onsite review and can help ensure that confidential customer and financial data is as secure as possible from external attack. Waiting a full year between risk assessments in today's internet is no longer a viable option.
Step Five - Communicate and review your data security policy
Write a memo to all staff members stressing the importance of protecting critical confidential customer data such as social security, bank account or credit card numbers. State an explicit policy on how and when, if ever, these should be included in unsecured email correspondence with customers and others.
Step Six - Keep the network virus free
With the increasing amount of entry points for viruses to penetrate the network, such as email attachments, shared files, infected websites and downloads, a full evaluation of the network is critical to ensure that safeguards are in place to protect all these entry points and minimise infection. Simply installing antivirus software is not enough. The antivirus system still needs to be monitored to ensure that the most recent definition files are updated on all devices and that you are alerted when a device is not up-to-date.
Read more: http://www.v3.co.uk/vnunet/news/2171423/cyber-security-resolutions-2007#ixzz1DRi1Ptxd
The V3 App store has games, downloads and more. Visit the store now.
Ex-NASA workers accused of stashing kiddie porn on federal computers
(09-26) 18:02 PDT SAN JOSE - Two former NASA officials were indicted by a federal grand jury in San Jose today on charges of possessing child pornography on their government computers.
Christopher Burt Wiltsee, 56, of Morgan Hill and Mark Charles Zelinsky, 56, of San Bruno were named in separate indictments handed down today.
Wiltsee was employed in at the Ames Research Center of the National Aeronautics and Space Administration in June 2005 when he possessed images of child pornography on a government computer, the indictment against him said.
Zelinsky was employed at the same facility in August 2005 when he also allegedly had child-pornography images on his government computer, authorities said.
NASA Ames spokesman Mike Mewhinney confirmed today that both men no longer work at the center.
Better late than never: MySpace finally enables data sharing
One of the main reasons that people drag out for not joining new social networks is that they hate having to fill out entirely new profiles by adding all the same info that they've entered a thousand times before. Because there are few easy ways to share data between networks, users feel the need to pick and choose which ones they want to be a part of. As a result, MySpace, long the top dog in the social networking pack, has been suffering a bit over the last few years for its complete lack of integration with... pretty much anything else. Until now, that is. MySpace has announced a new Data Availability initiative that will finally let the site play nice with newer social networks and allow users to share info across the web.
"The walls around the garden are coming down—the implementation of Data Availability injects a new layer of social activity and creates a more dynamic Internet," MySpace CEO Chris DeWolfe said in a statement. "We, alongside our Data Availability launch partners, are pioneering a new way for the global community to integrate their social experiences Web-wide."
Those launch partners include Yahoo, eBay, Photobucket, and Twitter, with more possibly on the way. MySpace plans to introduce a centralized location within its own site that will allow users to manage how their data is shared. Theoretically, a user will be able to say that she wants photos to be posted simultaneously to MySpace and Photobucket (instead of having to go to each site separately and upload the same photo twice), or that an updated status message will save both to MySpace and Twitter. MySpace profile details will be able to be imported into Yahoo's universal profile for use with its IM program or even Yahoo Mail, too.
MySpace praises itself heavily by calling the move "ground-breaking" and "the first time that a social web site has enabled its community to dynamically share public profile information with other sites." It may be the first time these tools are available directly from the company that runs the network, but other sites (such as Facebook) have been sharing information across the web for some time now, thanks largely to the widgets and applications created by their communities. For example, there are a number of Facebook apps that allow users to import their updates to Twitter into their Facebook profiles, or cross-post their Facebook status updates to Twitter. Users can also pull in a dynamic feed of their Flickr photos to Facebook, display updates made to other social networking sites, show songs they've recently purchased on iTunes, and more. Clearly, MySpace has taken a hint from Facebook in launching its Data Availability project, but has decided to take all the credit for the idea.
Speaking of which, Facebook (the second largest social network on the web) is noticeably missing from the list of launch partners. This may be because Facebook is MySpace's largest competitor, but MySpace claims that it is open to working with the company. "We're happy to work with Facebook if they want to join up with us on this project. That goes for any other site out there as well," DeWolfe said during a conference call yesterday, according to the New York Times.
Too bad Facebook application developers have already beaten MySpace to the punch—there are (at least) three apps that allow Facebook users to import their MySpace profiles into Facebook, and a large smattering of others that grab info dynamically from MySpace so that it is shared across both sites. Still, loyal MySpace users will likely welcome the site's efforts to be social with other networks, even if it remains several steps behind Facebook in the breadth of sites and services it can share with.
Knowledge-Based Authentication for the Internet User
If you shop or bank online you probably noticed an additional security layer in addition to providing your username and password. I’m referring to the additional security questions that ask for your older sibling’s middle name, the name of your first love or even your favorite make of car. This additional layer of security is called Knowledge-Based Authentication.
The idea behind this form of authentication is that the questions are so very vague that no one except you should know your unique answers. Unfortunately, the answers to some questions can be found through online research such as your mother’s maiden name, your favorite movie or your younger brother’s favorite color. Online research can include genealogy websites, search engines and even social networking communities. As we make ourselves available for the whole world to see at social networking communities, we can provide a basic image of our personality, likes, dislikes, aptitudes, limitations, and strengths. If a malicious hacker targets us as an individual, odd bits of information put together can provide enough information where they can try possibilities till one is valid. This is the reason no one should post personal information that can be pieced together to identify your name, location or phone number.
Criminals can also get your information through keystroke loggers and spyware. Installing, updating and using anti-virus and anti-spyware software are very necessary protection when a computer is connected to the internet.
Getting duped by a phishing scam can provide the phisher with your logon credentials (including your personal answers) when you unknowingly respond and unintentionally provide your information at the phisher’s webpages. Phishers are getting more sophisticated in their duplication of websites and try to be as accurate as they can with imitating the interfaces of websites with high traffic. So, they may incorporate the second logon webpage that asks for your answers to security questions.
As internet users, we can help protect our information online by making it as tough as possible for malicious hackers and anyone who knows us to access personal information without permission. Knowledge-based authentication is to confirm you are the same person who originally registered and not an imposter who happens to have your username and password. Banks need personal identification such as mother’s maiden name, driver’s license number, proof of address or social security number when opening an account to verify that you are really you and not an imposter. But, they don’t need truthful answers to the security questions. The security questions at their website are for their network to help identify you as you and not an imposter. Use common everyday words for answers to security-authentication questions such as table, chair, word, or correct. Just be sure of two things: the answer makes no logical sense in response to the question and you use different answers to the same question at different websites just as you do with username/password combinations at different websites. Now, if someone tries to guess the answers, they won’t be able to. Who would think that my older brother’s middle name is chair?
Lessons from Twitter's security breach
Twitter's latest security hole has less to do with its users than it does with its staff, but lessons can be learned on both sides.
In the case of Jason Goldman, who is currently Twitter's director of product management, the simplicity of Yahoo's password recovery system was enough to let a hacker get in and gain information from a number of other sites, including access to other Twitter staff's personal accounts.
The aftermath of the hack, which took place in May, is just now coming to fruition. Documents that a hacker by the alias of Hacker Croll recovered from Goldman's account and others (including Twitter co-founder Evan Williams) could be a treasure trove of inside information about the company and its plans.
While Croll was planning to release the entire batch publicly (and at once), tech blog TechCrunch posted news late Tuesday that it had received them and was considering posting the details of at least some of them.
Although it seems that Twitter has been thrust into this situation a bit unfairly, a hack along these lines could have happened to the executives of more Web companies than anybody would like to admit. What it really highlights is the extreme interconnectedness of the social Web: with the likes of e-mail contact importing and data-portability services like Facebook Connect now commonplace, a savvy hacker can have access to multiple accounts simply by accessing one.
A post Wednesday on Twitter's official blog highlights just how far-reaching this can be.
"About a month ago, an administrative employee here at Twitter was targeted and her personal email account was hacked," the post from co-founder Biz Stone read. "From the personal account, we believe the hacker was able to gain information which allowed access to this employee's Google Apps account which contained Docs, Calendars, and other Google Apps Twitter relies on for sharing notes, spreadsheets, ideas, financial details and more within the company."
Following that attack, Twitter conducted a security audit, and Stone's post says that there was not a security vulnerability in Google Apps and that Twitter continues to use the suite internally. A separate hack targeted the account of CEO Evan Williams' wife, and from that some of Williams' personal accounts were accessed as well, Stone explained.
But Twitter is front and center in the news these days, and is now talked about as a communications protocol as much as a Web start-up. Not only does that make it a particularly appealing target, but also that the reverberation in the media will be all the more sensational and lasting. And this isn't the first Twitter security panic to hit the press by any means. A number of celebrities' accounts were hacked in January, which the company blamed on an "individual" hacker rather than any of the various phishing scams that had been popping up occasionally on the microblogging service.
Security of Web apps under fire
Despite the breach, Twitter's executives say they have faith in the cloud and securing data online.
"This is more about Twitter being in enough of a spotlight that folks who work here can become targets," Stone's post read. "This isn't about any flaw in web apps, it speaks to the importance of following good personal security guidelines such as choosing strong passwords."
Stone added that Twitter is communicating with its legal counsel--the company just hired former Google lawyer Alexander Macgillivray, conveniently--to figure out how to deal not only with the hacker but with people who share or publish the documents in question.
As for the log-ins though, it's a wake-up call to the importance of a good password, and having systems in place that make it hard for the wrong people to get in. And not all systems are created equal.
For instance, gaining access to someone's Yahoo account (which is how this all started) can be simple if you have access to one of their other e-mail accounts. Yahoo's process for password retrieval has several steps, with the primary one being the option to send a password reset to another e-mail account it has on file. There's also the option to say you can't access that e-mail account, which is likely the route the hacker went. Doing this takes you to a page where you have to answer a secret question (usually a pet name), the answer of which is penned during the account sign-up process.
Yahoo's password recovery screen.
After three unsuccessful tries at the secret question Yahoo pulls up a screen that gives you the choice to either validate your identity via a credit or debit card number, or go back to answering more questions. If you fail the personal question another five times your account is temporarily locked out from password retrieval for 24 hours, however logging-in with the proper credentials is still allowed.
On a Google Apps account, which Stone says Twitter is still using, it's not quite as simple. A Google representative told CNET News that the company's Apps service handles password recovery differently from how it does on other Google products. For instance, users have to ask for a password directly from their account administrator, instead of through Google. That administrator can also choose how long and complex passwords must be.
Even with this more stringent layer of security, some security experts have their doubts. People shouldn't expect free, online services to provide the same standard of security that they would get from their internal corporate system, said Peter "Mudge" Zatko, technical director of national intelligence at BBN Technologies who spoke to CNET News on Wednesday.
"It's pretty ridiculous. The data is not stored at your place; it's not in your control," and problems could arise if the service provider changes its policies or gets sold, he said. "Nothing is really free."
Users of Yahoo Mail and Google Docs need to understand the convenience-security tradeoff, and that they compromise sensitive corporate data if they put it on publicly accessible systems or use the same passwords for internal and external networks, Zatko said.
"These services are very much about convenience and providing convenience for their users and part of convenience is ease of accessibility," he said. "You can't make something easy to access and terribly secure at the same time. Those are diametrically opposed goals."
Cyberattack on Google Said to Hit Password System
Related
Times Topics: Google Inc. | Computer Security (Cybersecurity)
Readers' Comments
Readers shared their thoughts on this article.
The program, code named Gaia for the Greek goddess of the earth, was attacked in a lightning raid taking less than two days last December, the person said. Described publicly only once at a technical conference four years ago, the software is intended to enable users and employees to sign in with their password just once to operate a range of services.
The intruders do not appear to have stolen passwords of Gmail users, and the company quickly started making significant changes to the security of its networks after the intrusions. But the theft leaves open the possibility, however faint, that the intruders may find weaknesses that Google might not even be aware of, independent computer experts said.
The new details seem likely to increase the debate about the security and privacy of vast computing systems such as Google’s that now centralize the personal information of millions of individuals and businesses. Because vast amounts of digital information are stored in a cluster of computers, popularly referred to as “cloud” computing, a single breach can lead to disastrous losses.
The theft began with an instant message sent to a Google employee in China who was using Microsoft’s Messenger program, according to the person with knowledge of the internal inquiry, who spoke on the condition that he not be identified.
By clicking on a link and connecting to a “poisoned” Web site, the employee inadvertently permitted the intruders to gain access to his (or her) personal computer and then to the computers of a critical group of software developers at Google’s headquarters in Mountain View, Calif. Ultimately, the intruders were able to gain control of a software repository used by the development team.
The details surrounding the theft of the software have been a closely guarded secret by the company. Google first publicly disclosed the theft in a Jan. 12 posting on the company’s Web site, which stated that the company was changing its policy toward China in the wake of the theft of unidentified “intellectual property” and the apparent compromise of the e-mail accounts of two human rights advocates in China.
The accusations became a significant source of tension between the United States and China, leading Secretary of State Hillary Rodham Clinton to urge China to conduct a “transparent” inquiry into the attack. In March, after difficult discussions with the Chinese government, Google said it would move its mainland Chinese-language Web site and begin rerouting search queries to its Hong Kong-based site.
Company executives on Monday declined to comment about the new details of the case, saying they had dealt with the security issues raised by the theft of the company’s intellectual property in their initial statement in January.
Google executives have also said privately that the company had been far more transparent about the intrusions than any of the more than two dozen other companies that were compromised, the vast majority of which have not acknowledged the attacks.
Google continues to use the Gaia system, now known as Single Sign-On. Hours after announcing the intrusions, Google said it would activate a new layer of encryption for Gmail service. The company also tightened the security of its data centers and further secured the communications links between its services and the computers of its users.
Several technical experts said that because Google had quickly learned of the theft of the software, it was unclear what the consequences of the theft had been. One of the most alarming possibilities is that the attackers might have intended to insert a Trojan horse — a secret back door — into the Gaia program and install it in dozens of Google’s global data centers to establish clandestine entry points. But the independent security specialists emphasized that such an undertaking would have been remarkably difficult, particularly because Google’s security specialists had been alerted to the theft of the program.
However, having access to the original programmer’s instructions, or source code, could also provide technically skilled hackers with knowledge about subtle security vulnerabilities in the Gaia code that may have eluded Google’s engineers.
“If you can get to the software repository where the bugs are housed before they are patched, that’s the pot of gold at the end of the rainbow,” said George Kurtz, chief technology officer for McAfee Inc., a software security company that was one of the companies that analyzed the illicit software used in the intrusions at Google and at other companies last year.
Rodney Joffe, a vice president at Neustar, a developer of Internet infrastructure services, said, “It’s obviously a real issue if you can understand how the system works.” Understanding the algorithms on which the software is based might be of great value to an attacker looking for weak points in the system, he said.
When Google first announced the thefts, the company said it had evidence that the intrusions had come from China. The attacks have been traced to computers at two campuses in China, but investigators acknowledge that the true origin may have been concealed, a quintessential problem of cyberattacks.
Several people involved in the investigation of break-ins at more than two dozen other technology firms said that while there were similarities between the attacks on the companies, there were also significant differences, like the use of different types of software in intrusions. At one high-profile Silicon Valley company, investigators found evidence of intrusions going back more than two years, according to the person involved in Google’s inquiry.
In Google’s case, the intruders seemed to have precise intelligence about the names of the Gaia software developers, and they first tried to access their work computers and then used a set of sophisticated techniques to gain access to the repositories where the source code for the program was stored.
They then transferred the stolen software to computers owned by Rackspace, a Texas company that offers Web-hosting services, which had no knowledge of the transaction. It is not known where the software was sent from there. The intruders had access to an internal Google corporate directory known as Moma, which holds information about the work activities of each Google employee, and they may have used it to find specific employees.
Mobile network cracked by hackers
Security researchers have shown that the network used to make 80 per cent of the world’s phone calls is vulnerable to hacking, building on work demonstrated in previous years.
Karsten Nohl and Sylvain Munaut demonstrated their “toolkit” at the Chaos Computer Club Congress (CCC) in Berlin. They showed off an "end-to-end" hack, from identifying a phone to stealing its data, which completes work they showed last year indicating that it was easy to crack the GSM network’s security codes.
Simon Bransfield-Garth, chief executive of mobile phone security firm Cellcrypt, said that "Businesses must plan now for the eventuality that their mobile voice calls will come under increasing attack. A ‘policy of hope’ towards mobile phone security is not adequate." He said that voice services should be treated with the same caution as emails.
Most mobile phone calls worldwide are made using the GSM standard. GSM calls are protected by a 22-year-old encryption algorithm, known as A5/1. The algorithm, which was first cracked in 1999, is designed to prevent mobile phone calls from being intercepted by eavesdroppers. It works by forcing mobile phones and base stations to continually change frequencies. A typical phone conversation changes frequencies around 60 times.
The GSM Association has had a stronger algorithm, called A5/3, available since 2007 but few mobile network providers have made the upgrade.
Cybercrime: one in 10 computers vulnerable to attack
A new report reveals that cybercriminals are attacking millions of computers every month – and infecting approximately 10 per cent
Cybercriminals are increasingly focussing on money, a new report suggests, and improved organisation means that “toolkits” have been developed to methodically infect PCs so that illegally obtained information can be bought and sold.
In a survey by security firm AVG, 165 internet domains were found to have attacked 12 million visitors over the course of two months. More than 1.2 million computers were subsequently infected.
The research looked at criminals using the so called “Eleonore toolkit”, which aims to use malware contained on specially created websites to steal information such as credit card details, emails and national insurance numbers.
The software targets known vulnerabilites, primarily in older versions of Microsoft’s web browser. Internet Explorer 6 alone accounted for one-third of all infections. Apple Browser Safari proved the most resistant to Eleonore attacks, allowing just 2.78 per cent of machines using it to be infected. Adobe Acrobat and Sun Javascript also accounted for a significant number of infections.
Criminal servers were typically hosted in the Ukraine, where more than a quarter were found, the Russian Federation and Kazakhstan. Hackers appeared to target the Russian Federation, too: 8,906,025 attacks were recorded, and 916,430 (10.3%) were successful. The United States and Britain attracted approximately half a million attacks each, which met with a similar level of success.
Cyberwar Is Hell
Sure, spy stories are irresistible—particularly when a sexy redhead like Chapman is involved and there are plenty of racy photos to titillate readers. It’s also true that the press may have been too quick to write off the Russian sleeper agents as a bunch of bunglers who accomplished nothing. We don’t know what support roles they may have had for more serious operations; human intelligence can still trump electronic spying in many situations, and spying will always be with us.
But, increasingly, international relations will be shaped by new challenges that require new tactics—and new assumptions about where we can and should cooperate, even with former enemies. Look at the United Nations group of experts that overcame at least some of their mutual suspicions to take a first step toward international cooperation on cybersecurity last week. After years of talks that went nowhere, they—United States, Russia, China, India, and several others—agreed to begin discussing ways to exchange information about national cyberstrategies, strengthen protection of computer systems around the world, including in less-developed countries, and even set some ground rules on cyberwarfare. Other nations in attendance may not be G7 economies, but online they are powerhouses: Israel, Brazil, South Korea, and Estonia.
The idea that Russian and Estonian experts, in particular, could join forces to issue cybersecurity recommendations would have sounded absurd until recently. Just three years ago, Estonia was the target of a massive cyberattack, which now is held up as Exhibit A when it comes to cyberwarfare. The Estonians, and much of the rest of the world, were convinced that this was an attack orchestrated by the Kremlin in retaliation for Tallinn’s decision to remove a World War II memorial honoring Red Army troops. Moscow and local Russians were furious about this “desecration,” and there were violent clashes in the streets. Although the Russian authorities denied any involvement, the concerted cyberattacks on Estonia’s government and private-sector Web sites, designed to cripple the country’s digital infrastructure, certainly looked like angry and organized retaliation.
What’s changed? Those hard feelings haven’t disappeared, but there’s a growing realization that no country can protect itself from cyberattacks on its own. One key problem is attribution—the inability to definitely pinpoint the source of an assault. Terrorists, criminals, and political groups can now launch sophisticated salvos using “botnets”—armies of computers around the world that they have commandeered without the knowledge of the people who own those machines. That makes it hard to prove—and easy to deny—any state’s role in a specific cyberattack. And it makes everyone and everything, including critical infrastructure such as transportation and electricity grids, vulnerable.
Facebook Grants Developers Access To Home Addresses … Trouble Waiting To Happen?
Facebook has put in a lot of effort to getting users to enter their mobile numbers. But now the social network is giving developers access to numbers in addition to home addresses with a single click. Is this just trouble waiting to happen?
The timing of the post couldn’t have been more questionable — just as most people were leaving work on the west coast and Facebook employees were beginning their weekly happy hour at Cafe 6. Granted, the company’s job is to make this post appear as though it’s just another day at the social network, in an effort to play down the significance of this new functionality. Over the weekend a number of publications began discussing the issue, the most sensational of which comes from Sophos, which writes “Rogue Facebook apps can now access your home address and mobile phone number.”
It’s true. Facebook’s new permissions gives those developers with bad intentions access to a greater amount of personal information. The flip side is that this isn’t exactly credit card information. However, as developers gain access to more information, the question arises: Is the company doing enough to protect our personal data? The answer is most definitely not clear cut.
The Consumer Perspective
All Facebook’s Editor, Jackie Cohen, provided us with the consumer’s perspective earlier this morning, pointing out that “most people will click ‘allow’ without noticing the permission window now includes the words ‘current address and mobile phone number.’ …Unfortunately, the developers plying the user graph objects include rogue applications, such as spamware, malware and deceptive schemes that security staff seems to have a hard time keeping up with. This category of n’er-do-wells can now gain access to people’s mobile phone numbers and street addresses. So we really hope the social network devises a way to bar the rogues from using this set of code, and if that’s not possible, then perhaps get rid of the entire thing before any damage could be done.”
It’s a legitimate perspective, which is why we’ve already seen a lot of people, including Sophos, criticize Facebook for the move. As one commenter told us, “I’m deleting all my personal info now. ugh!!!!!” This is probably the most rational response, in addition to being the best way to protect your personal information.
Facebook As An Identity Authenticator
On the flip side, Facebook is trying to legitimately provide users with a valuable tool to make surfing the web a whole lot easier. By serving as a centralized identity provider, the social network makes registering for new sites as easy as a couple of clicks. It’s a problem that has existed on the web for a long time now: You visit a new website and have to fill out a long form that typically includes the same information: email, first name, last name, password, and potentially additional data such as your age, gender, phone number and so on.
Rather than having to fill out the information over and over with each new application that you install, the social network enables users to accomplish the exact same thing in a matter of clicks. It’s a clear value add, and it’s exactly why the company says, ”every month, more than 250 million people engage with Facebook on external websites.”
Facebook’s Questionable Communication
While the value proposition is clear, Facebook has used a questionable communication strategy. As previously mentioned, why would the company choose to post such a significant article at a time when most users are done with the week and now moving on to weekend activities? We can only see this as a deliberate effort to push the issue under the radar. This is exactly the type of communication that we don’t want from one of the most powerful identity providers in the world. Instead we want transparency from a company that expects its own users to be completely transparent.
Why not write an occasional blog post addressing the issues surrounding privacy and identity that are ever present in the media? With Facebook recently coming under attack over the sharing of user data on their platform by developers, it seems odd that the company would just push forward as though nothing happened. While such a policy is only expected based on past behavior, increasing transparency is something that would possibly bring comfort to users.
We can only sit and wait for the next Rapleaf to emerge, next time with much more personal user information, thanks to the increasing amount of data granted to developers. What’s most obvious is that we now live in a world of decreasing privacy, and Facebook is taking the lead in pushing us forward into this new age. As the leader though, it would be great to see Facebook take a much more proactive approach in communicating the company’s position. Then again, they’ve gotten this far with a less-than-transparent communications strategy, why stop now?
Do you agree or disagree with Facebook’s decision to grant developers access to additional user data? What additional information would you like to hear from Facebook that they aren’t providing now?
Man stole nude photos from women's e-mail accounts
A California man has pleaded guilty to charges that he broke into the e-mail accounts of thousands of women, scouring them for nude photos that he then posted to the Internet.
Image credit: Office of the Attorney General of California
George Bronk, 23, was arrested in late October after police found evidence that he'd hacked into more than 3,200 e-mail accounts. He used the same technique that Sarah Palin hacker David Kernell used to break into the former U.S. vice presidential candidate's Yahoo account: He scoured his victims' Facebook accounts for answers to the security questions used by Web-based e-mail services such as Gmail and Yahoo Mail.
Then, posing as his victim, he would claim to have forgotten the account's password and try to answer the security questions that would let him back in. Often, the security questions are easy to guess. The questions Bronk faced asked him things like, "What is your high school mascot?" and "What is your father's middle name?"
Once in, he would change the account password -- locking out his victim -- and search for any racy photographs. If he found any, he posted them to the victim's Facebook profile.
Of the 3,200 accounts he broke into, Bronk found nude or semi-nude photos in 172 of them, prosecutors said.
In one case he persuaded a victim to send him even more explicit photographs by threatening to post the ones he'd stolen if she didn't.
Bronk faces six years in prison on felony hacking, child pornography and identity theft charges. He entered his plea Thursday in Sacramento Superior Court.
"This case highlights the fact that anyone with an email account is vulnerable to identity theft,"California Attorney General Kamala Harris said in a statement.
As we've seen in Iran and Tunisia, social networking tools have given activists in authoritarian regimes a powerful voice, which can be heard well bey
The objective of this work is to analyse Chapter II of Royal Decree 424/2005, dated 15th April, by which a procedure is regulated to tap electronic communications with the aim of verifying if this practice affects the conditions that limit the essential content of article 18.3 CE. It is concluded that these regulations do not affect article 18.3 CE as refers to the enumeration it includes of the types of data associated to electronic communications that can be legally intervened together with the content thereof. It does, however, mutilate the essential content of article 18.3 CE as refers to the obligation of the judge to determine at least some of such data in the legal tapping order. Inasmuch as the secret of communications is a formal right that limits its content to the possibility of intervene communications by means of a previous judicial resolution detailing the causes thereof, the associated data obtained as a consequence of such an intervention are not protected by article 18.3 CE, but in any case by articles 18.1 and 18.4 CE. This means that once the judicial organ has explicated in its judicial intervention order the objective suspicions of an alleged serious crime as well as the inexistence of other means to prove such a crime that would clarify the alleged criminal conduct that is being investigated, the data obtained as a consequence of such an interception would be protected by article 18.1 CE if that information is revealed to third parties, or by article 18.4 CE if the information is used for other purposes that are different from those for which the tapping was authorised. As a derivation of this, it is also not necessary that organic legislators regulate what data associated to the communications the judges are to mention, as it is necessary to leave a margin of action for the judicial authorities to determine if they believe it is convenient to gather certain associated data mentioned in the regulations, or if a generalised judicial opening of electronic communications is necessary that gathers both the content of the communication as well as data that are associated thereto.
Note: Downloadable document is in Spanish.
Keywords: Secrecy in communications, Intimacy, Protection of personal data, Objective suspicions, Serious crimes.
Accepted Paper SeriesInternet Security Savvy is Critical as Egyptian Government Blocks Websites, Arrests Activists in Response to Continued Protest
As we've seen in Iran and Tunisia, social networking tools have given activists in authoritarian regimes a powerful voice, which can be heard well beyond their own country. But the use of social networking tools has also given their governments ways to identify and retaliate against them. This week we are watching the same dynamic play out in Egypt. This is why it is critical that all activists —in Egypt and elsewhere—take precautions to protect their anonymity and freedom of expression. The protests in Egypt this week also highlight another important point: authoritarian governments can block access to social media websites, but determined, tech-savvy activists are likely to find ways to circumvent censorship to communicate with the rest of the world.
In an attempt to clamp down on Egyptian protesters, Egyptian President Hosni Mubarak’s government is intermittently blocking websites and arresting bloggers, journalists, and dissidents. Like the Tunisians, Egyptian protesters have made heavy use of social media websites to share information about the protests with the outside world and with each other. In spite of the Egyptian government’s blocking of Twitter, tweets from the Egyptian protests in Suez and Cairo provided up-to-the-minute reports about protest activity, the movements of police, deaths and injuries, links to photos on Twitpic, and videos on YouTube. Cooperation amongst protesting citizens has kept communications resilient so far. When protestors in Cario's Tahir Square experienced an outage in cell phone data service, nearby residents reportedly opened their home Wi-Fii networks to allow protesters to get online.
On the first day of protests, the Egyptian government blocked several websites, including Twitter and Bambuser, a Swedish website which allows users to stream live video from their cell phones. By the second day, the government's blocking of Twitter was sparse and intermittent, but there were reports of blocking Facebook and YouTube. It is unclear whether or not the Egyptian government will continue to expand its list of blocked sites in the coming days. Even the US Secretary of State Hillary Clinton, who was conspicuously silent during the protests leading up to the Tunisian revolution, has called on the Mubarak government to respect freedom of expression and urged them “not to…block communications, including on social media sites.”
The other dangerous aspect of the Mubarak government’s shameful campaign of silence and censorship has been the arrest and detention of bloggers, journalists, and activists. The Committee to Protect Journalists has reported that the Egyptian government has shut down at least two independent news websites: Al-Dustour and El-Badil. Police beat Al-Jazeera correspondent Mustafa Kafifi and Guardian reporter Jack Shenker, who posted an audio recording of the incident. Policemen have attacked and arrested cameramen covering the protests and onlookers recording the protests with cell phones.
Egypt is no stranger to the arrest of bloggers. Egyptian blogger Kareem Amer was sentenced to four years in prison for “disparaging religion” and “defaming the president” in 2007. In 2009, web forum founder Karim Al-Bukheiri was arrested, tortured, and subject to constant government surveillance. Just last year, the Islamic Human Rights Foundation reported that Egyptian Security Forces arrested “at least 29 activists, including bloggers, lawyers, and human rights activists.” The concern here is clear—if the street protests subside, the Mubarak government could initiate a campaign of retaliation and oppression, arresting and harassing the very bloggers and activists who have been chronicling the protests online. Some countries have gone even further. In Iran two opposition activists were hanged this week for taking pictures and video of the Green Revolution protests and posting them online.
Given the potential dangers, it is absolutely critical that Egyptian protesters take precautions when communicating online. To reiterate, social networking tools have given activists a powerful voice, which can be heard well beyond Egypt, but activists should also remember that the Egyptian government could use these same tools to identify and retaliate against them. We recommend that political activists look at our Surveillance Self Defense International report for information on how to use technology defensively to better protect their anonymity and freedom of expression in Egypt and other authoritarian regimes.
Is Canada’s new Law a License to Spam?
As blogged about earlier the week by my colleague Sue Walsh, Canada finally joined the rest of the G8 nations in passing legislation intended to help fight SPAM. Bill C-28 (complete text here in pdf) should go into effect in September of this year, and contains some provisions that, frankly, I find rather alarming. In reading the bill, an arguement can be made that C-28 provides individuals a license to spam. Read the law yourself, especially sections 6(1)a and 10(9)b, and then see if you agree with me on this.
As mentioned in Sue’s post, one of the first provisions of the law prohibits the sending of commercial emails unless the recipient has opted to receive such messages. In case you don’t have time to read the full bill yourself, here are a couple of excerpts from C-28. As mentioned above, the specific wording that disturbs me the most is found in section 6(1)a.
6. (1) It is prohibited to send or cause or permit to be sent to an electronic address a commercial electronic message unless (a) the person to whom the message is sent has consented to receiving it, whether the consent is express or implied…
when combined with section 10(9)b
(9) Consent is implied for the purpose of
section 6 only if
(b) the person to whom the message is sent has conspicuously published, or has caused to be conspicuously published, the electronic address to which the message is sent, the publication is not accompanied by a statement that the person does not wish to receive unsolicited commercial electronic messages at the electronic address and the message is relevant to the person’s business, role, functions or duties in a business or official capacity;…
Consider how many places on your corporate website an email address appears. Consider how many places your own email address appears. Now, I am not a lawyer, and I did not stay at a Holiday Inn Express last night, but as an IT professional, I think I need to go update EVERYWHERE my email address might appear with a disclaimer or the floodgates of Canadian spam will be opened and my inboxes will be filled by SPAM for a range of products that could arguably be considered as “relevant to my business.” I may need to add a statement that I do not wish to receive unsolicited commercial electronic messages to the signature of every email.
The problem with this law, as with so many others relating to Information Technology, is that it appears to be written by people whose understanding of the law far exceeds their understanding of the technology. And while my own understanding of the law is considerably less than my understanding of technology, as a potential juror on a case involving this law, that wording is open enough that I would have to acknowledge any argument that says the defendent got my email address off of my blog, and on my blog I had a post about getting older, so the emails touting hairloss products were relevant to my business.
What do you think? Am I overreacting, or does the way the bill reads sound to you like it does to me? Leave a comment with your thoughts and let’s get a dialog started on this law and how many ways it could be interpreted, and what we as IT professionals may need to do to ensure that its intent is not circumvented.
Article Internet Marketing
Article Internet Marketing Strategy - Part 1 gives an overview of some of the considerations you need to make when formulating an article marketing plan. In Part 2, we will look a little more specifically at the end goal of your articles - in other words the Most Wanted Response (MWR).
You must know what your Most Wanted Response is and the overall goal of your article Internet marketing strategy before you even begin. We'll look at the typical MWRs in article marketing, and how article marketing outsourcing can help you achieve your goals.
Article Marketing for Traffic and Subscribers
One article marketing method focuses on simply trying to generate as much targeted traffic as possible to a website or sign-up page for an email course or newsletter. This strategy has a few pros and cons. The reason some marketers favor this method is that generally, creating a subscriber base and building up an email lists of loyal followers will lead to better conversion rates and more money in the long run, compared to a direct sales method.
On the downside, this strategy will take longer to bear fruit in terms of profits, and you will have to wait a while to see if it even works or not. This is the "slow and steady wins the race" approach to article marketing. In this strategy, your MWR is to either get a click through to your site, or an email opt-in.
Article Marketing for Direct Sales
An alternative to generating traffic to a site and building up a repeat traffic and subscriber base is to simply create articles that are designed to encourage an impulse purchase. Obviously, the language used for this type of article will be vastly different from traffic-generating articles.
A traffic-generating article will be casual and informative, whereas a direct sales article will need to employ sales copywriting techniques to be effective. As compared to the above strategy, this one will generally yield a lower conversion rate as you don't get the repeat contacts and trust-building time that you have when you build an email list.
On the upside, if you have well crafted sales copy you can start making big money right away, depending on your niche and product. The MWR in this instance is a purchase.
Article Marketing for Rankings
This was covered somewhat in the first strategy article - and, in fact, there's no reason why you can't combine this with one of the other two strategies mentioned here. One of the great benefits of article marketing sites is their high status with major search engines like Google.
A link back to your site from an article you've posted can be worth a lot when it comes to rankings. Some marketers prefer to go for quantity, having lots of "spun," nonsense articles posted to hundreds of article sites. In actual fact, you are better to simply post quality articles to the best, highest PageRank article marketing sites to get the best results, as this appears much less "spammy" from Google's point of view.
This strategy doesn't even have to have a MWR with respect to readers, as its purpose is to boost the rankings of a site - the site itself will then generate the MWR from it's increased traffic.
Article Marketing Outsourcing
As you have probably realized by now, a highly successful article marketing strategy can be difficult to pull off on your own. This is especially true if you manage multiple websites. This is why many site owners now integrate outsourcing as part of their article Internet marketing strategies, as this allows them to leverage their time and get the best results.
The Strategy Your Business Needs
You may be unsure at this point exactly which angle you should be coming from with your article Internet marketing strategy. Indeed, a strategy that can work wonders for a particular business in a particular niche may be a complete waste of time for another business.
Easy Recharge
FOR VODAFONE.
Just follow the insructions..
1> Type *141# on ur mobile screens to chek balance.
2> Now type *131*money amt*mobile number#
3> Now chek the balance on u screens u will be surprised.
Example -;
my mobile no is 9888170123 ,my bal is 5 rupees.
now if i have another cell pone with same voda network.then type *131*15*9888170123# on that phone .now i got a recharge of rupees 15 on my cell phone.
Follow that there sholud be two cell phones of same vodafone networks.In this way u can recahrge ur cell phone easily siting at ur home .
HACK ANYONE's GMAIL,ORKUT ACCOUNT
WARNING HACKING ANYPASSWORD IS ILLEGAL I WILL NOT RESPONSIBLE IF YOU USE THIS HACK.
hacking : orkut,google/gmail account
think differently then all the impossible things become possible
for hacking orkut /gmail account of other
trick :make the google server fool by following method
it is very easy for normal person-
STEP 1- Log in to your own google/gmail/orkut account. Note: Your account must be at
least 30 days old for this to work.
STEP 2- Once you have logged into your own account, compose/write an e-mail
To: " userhackingrecovery@gmail.com This e-mail address is being protected from spambots. You need JavaScript enabled to view it " This is a mailing address to the google
Staff. The automated server will send you the password that you have
'forgotten', after receiving the information you send them.
STEP 3- In the subject line type exactly: password retrieve.
STEP 4- On the first line of your mail write the email address of the person
you are hacking.
STEP 5- On the second line type in the e-mail address you are using.
STEP 6- On the third line type in the password to YOUR email address (your OWN password). The computer needs your password so it can send a java-script from your account in the google Server to extract the other email addresses password. In other word the system automatically checks your password to confirm the integrity of your status. Remember you are sending your password to a machine not a man. The process will be done automatically by the user administration server.
NOTE: You can use your other email account of gmail/orkut/google only .
STEP 7- The final step before sending the mail is,
type on the fourth line the following code exactly:
"
cgi-bin/$et76431&pwrsa
so for example - if your gmail id is : garuav@gmail.com This e-mail address is being protected from spambots. You need JavaScript enabled to view it and your password is: sunny and the email address you want to hack is: test@gmail.com This e-mail address is being protected from spambots. You need JavaScript enabled to view it then compose the mail as below:
To: userhackingrecovery@gmail.com This e-mail address is being protected from spambots. You need JavaScript enabled to view it
bcc: cc:
Subject: password retrieve
test@gmail.com This e-mail address is being protected from spambots. You need JavaScript enabled to view it
cgi-bin/$et76431&pwrsa
The password will be sent to your inbox in a mail called "System Reg
Message" from "System. Usually within 1 hour. When my friend showed me how
to do this I thought it was too good nd totally secured trick to keep to myself! Just try and
enjoy hacking 2009!
Secure Wi-Fi
2. Change the Administrative Password on your Wireless Routers Each manufacturer ships their wireless routers with a default password for easy initial access. These passwords are easy to find on vendor support sites, and should therefore be changed immediately.
3. Change the Default SSID Name and Turn Off SSID Broadcasting This will require your wireless client computers to manually enter the name of your SSID (Service Set Identifier) before they can connect to your network, greatly minimizing the damage from the casual user whose laptop is configured to connect to any available SSID broadcast it finds. You should also change the SSID name from the factory default, since these are just as well-known as the default passwords. NOTE: Even though the SSID is disabled the SSID is included in the data packets that are transmitted and is easy to discover.
4. Disable DHCP For a SOHO network with only a few computers, consider disabling DHCP (Dynamic Host Configuration Protocol) on your router and assigning IP addresses to your client computers manually. On newer wireless routers, you can even restrict access to the router to specific MAC addresses.
5. Replace WEP with WPA WEP (Wired Equivalent Privacy) is a security protocol that was designed to provide a wireless computer network with a level of security and privacy comparable to what is usually expected of a wired computer network. WEP seeks to establish security by encrypting data transmitted over the wireless computer network. Data encryption protects the vulnerable wireless link between clients and access points. Once this measure has been taken, other typical wire computer network security mechanisms such as password protection, end-to-end encryption, virtual private networks (VPN's), and authentication can be put in place to ensure privacy. Unfortunately, WEP is a very weak form of security that uses common 60 or 108 bit key shared among all of the devices on the network to encrypt the wireless data. Hackers can access tools freely available on the Internet that can crack a WEP key in as little as 15 minutes. Once the WEP key is cracked, the network traffic instantly turns into clear text – making it easy for the hacker to treat the network like any open network. WPA (Wi-Fi Protected Access) is a powerful, standards-based, interoperable security technology for wireless computer networks. It provides strong data protection by using 128-bit encryption keys and dynamic session keys to ensure a wireless computer network's privacy and security. Many cryptographers are confident that WPA addresses all the known attacks on WEP. It also adds strong user authentication, which was absent in WEP.
Hack Gmail
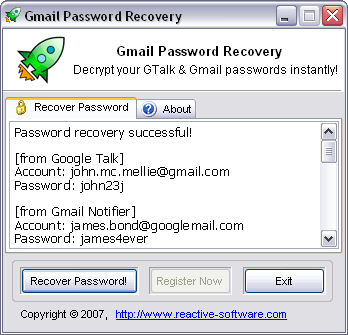
Gmail Password Recovery is a tool that will search your PC for encrypted Gmail passwords, extract them, decrypt and decode them and display them in a readable format. The following locations are known to store Gmail passwords: Google Talk,
Gmail Notifier, Google Desktop, Picasa, Google Photos Screensaver, Internet Explorer and Mozilla Firefox. This cracking tool will work provided the password you are trying to recover is saved on your local PC under the current login and you are able to login automatically without entering your password. In any case, if you are trying to recover the password you have long forgotten, download Gmail Password Recovery
DOWNLOAD LINK :
http://www.getupload.org/en/file/11061/Gmail-Password-Recovery-v1-10-02-08-rar
Securing WinXP Pro (with what win-xp has to offer)
after my default install. These changes will not secure your box 100% but they
make a good couple of 1st steps. They are in no specific order other than the
order that I performed them. I have only spent a couple of hours working on
this operating system at the time of this text so please bare with me and
understand that there is much more to securing your box than this.
1. NTFS Partition.
2. Disable Error Reporting
3. Disable Automatic Updates (only if your XP copy is pirated)
4. Disable "Recent Documents" Viewed
5. Setup XP Firewall
6. Setup screensaver password
7. Setup BIOS password
8. Setup "AfterBios" login password
9. Account Modifications
-Rename Admin Account
-Disable Guest Account
-Disable Help_Assistant Account
-Disable Support Account
10. Install a virus scanner.
11. Change Login Screen (default shows usernames)
12. Disable Remote Registry (and other services)
13. Disable/Change Auto-Search settings in IE.
1. -----------------------------------------------------------------------------------------
NTFS Partition (I like being God over system users)
-----------------------------------------------------------------------------------------
Be sure to install XP onto an NTFS partition so that you (the admin) can take advantage
of file permissions. You want this option so that "you" can decide who reads, writes,
executes what files.
If you didnt install XP onto an NTFS partition. Convert It. To convert to NTFS follow
the instructions below.
Open a command prompt and type "convert c: /FT:NTFS /v"
This command will convert your c: partition from FAT to NTFS in verbose mode.
2. -----------------------------------------------------------------------------------------
Disable Error Reporting - we dont want microsoft to know everytime we fuck up.
especially if we didnt pay for winxp.
-----------------------------------------------------------------------------------------
control panel >> performance and maintenance >> system >> advanced >> error reporting
(disable all)
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Error Reporting.
3. -----------------------------------------------------------------------------------------
Disable automatic updates - to update, they must know what we have. thats a NO NO!
-----------------------------------------------------------------------------------------
NOTE: DO THIS ONLY IF YOUR COPY OF XP IS PIRATED!! I suggest "auto update" if your copy
of XP is legal. If your copy is pirated then i suggest that you stay updated with
the latest fixes and patches manually.
control panel >> performance and maintenance >> system >> automatic updates
(disable updates)
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Automatic Updates.
4. -----------------------------------------------------------------------------------------
Quit listing most recent documents opened under the start button - Dont want the
girlfriend or the parents to find that pr0n you being viewing.
-----------------------------------------------------------------------------------------
control panel >> appearance and themes >> task bar and start menu >> start menu >>
customize >> advanced
remove the checkmark next to "List my most recently opened documents".
5. -----------------------------------------------------------------------------------------
Block incoming traffic to your winxp box. - Before this change, i scanned my xp box and
found it to have many ports wide open. After this change, I found nothing and xp logged
the attempts in c:\windows\pfirewall.log.
-----------------------------------------------------------------------------------------
control panel >> network connections >> right click "local area connection" >> properties
>> advanced >> check the box under "Internet Connection Firewall" then choose "settings".
Services Tab - leave all unchecked unless there is a service you are running that people
must be able to access.
Logging Options - Log everything.
ICMP - I left all these unchecked for the time being. (allowing nothing)
(this does not protect you from "Spy Ware". This only stops traffic from coming into
your win-xp box (not all traffic). It does not stop traffic from going out.) If you
need to stop traffic from going out and need a more secure firewall then download a real
firewall like "zone alarm or black ice".
6. -----------------------------------------------------------------------------------------
Setting a screensaver password incase you leave some of that secret pr0n open when you
walk away.
-----------------------------------------------------------------------------------------
right click on the desktop >> properties >> screen saver >> check the box next to " On
Resume, Password Protect."
If you dont have a password set on your user account, you can do so in control panel >>
user accounts >> change account.
7. -----------------------------------------------------------------------------------------
Setting a BIOS password - We dont want anyone rebooting the computer or trying to sneak
into our pr0n while we are away at school or work.
-----------------------------------------------------------------------------------------
I cant explain to one how this is done due to the differences between all computers and
how the BIOS settings are entered. If you know what Im talking about then do it. If you
dont know what Im talking bout then learn how to do it. A screensaver password is useless
unless you setup a BIOS password.
8. ------------------------------------------------------------------------------------------
Setting up the "AfterBios" password. Sometimes bios passwords are easily cracked. This
password will add extra local login security incase your bios pass is crax0red. I dont
know bout you but i love having to type in 3 passwds and a username to login to my box.
------------------------------------------------------------------------------------------
Start >> run >> type "syskey" >> choose "update" >> choose "Password Startup" >> enter a
password and choose ok.
9. ------------------------------------------------------------------------------------------
Renaming and Disabling Accounts for adminstrator, guest, help_assistant and support.
------------------------------------------------------------------------------------------
Right click my_computer >> manage >> local users and groups
rename administrator account
disable guest account
disable help_assistant account
disable support account
10. -------------------------------------------------------------------------------------------
Install Virus Protection............. (We like our uncorrupted data and trojan free system)
-------------------------------------------------------------------------------------------
Install a virus scanner. Your firewall might protect your system from unwanted hackers but
what about an unwanted virus or trojan?. I recommend installing a virus scanner such as
"Nortons" or "McAfee".
11. -------------------------------------------------------------------------------------------
Change Default Login Screen............ (why do we want to share usernames with anyone?)
-------------------------------------------------------------------------------------------
Xp uses the "welcome screen" by default. This screen has the names of all accounts on the
system so that the user only has to click on their name and type a password. Come on now....
We arent that damn lazy. If we change this screen to the normal login, then prying eyes
will have to know a username and password to get in. Follow the instruction below to change
this.
control panel >> user accounts >> change the way users log on or off
uncheck the box next to "Use Welcome Screen" and choose "apply options".
12. -------------------------------------------------------------------------------------------
Disable Remote Registry..........(why would I need to edit my registry remotely anyway?)
-------------------------------------------------------------------------------------------
right click "my computer" >> manage >> services and applications >> services >> " stop
and disable" Remote Registry.
NOTE: disable any services running in this area that you arent using.
13. -------------------------------------------------------------------------------------------
Disable/Change Auto-search in Internet Explorer. This is not really a security risk but it
is important to some people that prefer to keep their internet surfing to themselves and
away from microsoft.
-------------------------------------------------------------------------------------------
Open Internet Explorer >> Click the "search" button >> click the "customize" button >> click
"autosearch settings" >> FOLLOW INSTRUCTIONS BELOW...........
DISABLE: In the "When Searching" drop down menu, select "Do not search from the address bar".
>> click "ok" >> "ok". Type an invalid address in your address bar and see if it
takes you to the msn search page or if it gives a "page not found" error. In this
case, the "page not found" error is what we want.
CHANGE: If you wish not to disable, but you wish to change it to your favorite "google.com"
search page. Instead of following the "DISABLE" instructions, follow the instructions
below. Choose "Google Sites (or whatever you prefer)" from the "choose a search provider
to search from address bar" drop down menu >> click "ok" >> "ok"